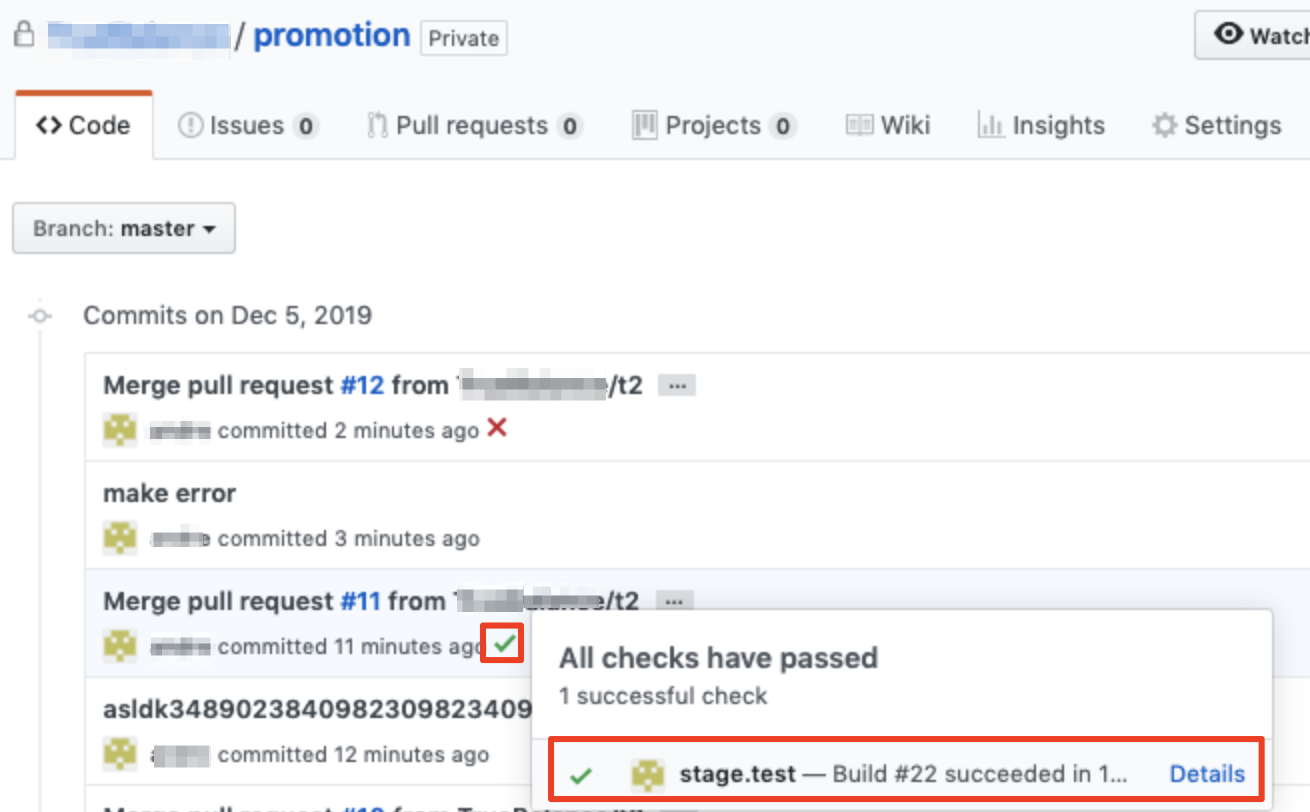
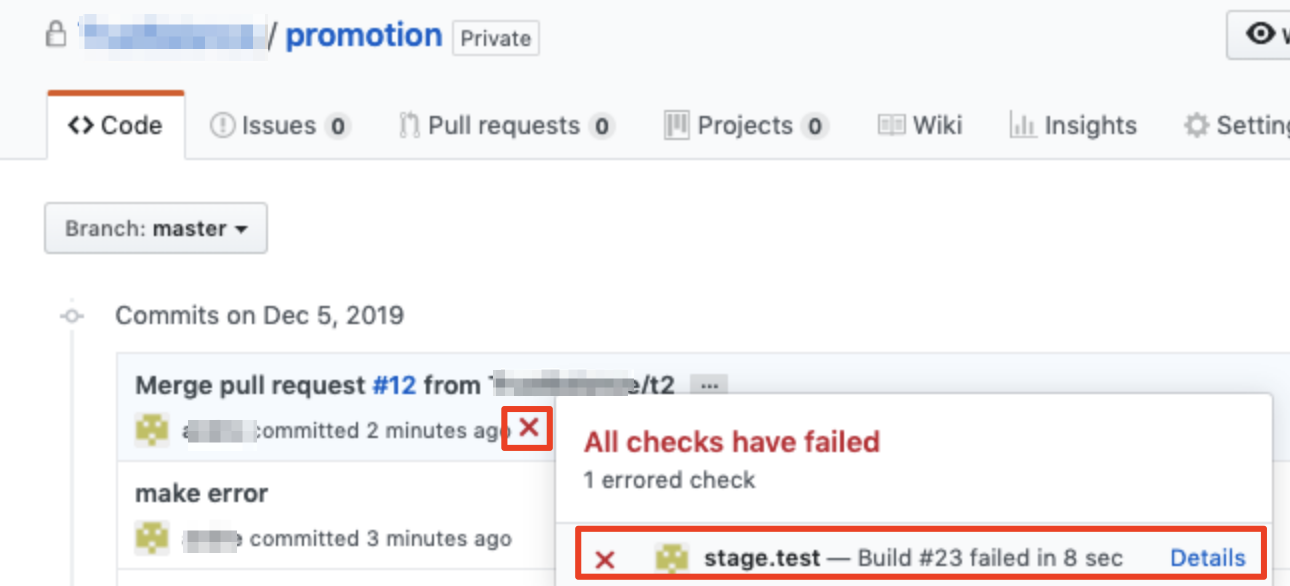
Kerberos user management sample flask code.
You could re-use this code for Kerberos host management as well
@app.route('/krb/user/<username>', methods=['GET', 'DELETE', 'POST', 'PUT'])
def userAPI(username):
result_code = "success"
result_message = "ok"
if request.method == 'GET':
cmd = "/usr/bin/kadmin -p account/admin -w ADminP@ssW0rd -q \"getprinc " + username + "\""
elif request.method == 'POST':
cmd = "/usr/bin/kadmin -p account/admin -w ADminP@ssW0rd -q \"addprinc -policy bhero -pw " + username + "123!@# " + username + "\""
elif request.method == 'DELETE':
cmd = "/usr/bin/kadmin -p account/admin -w ADminP@ssW0rd -q \"delprinc -force " + username + "\""
elif request.method == 'PUT':
password = username + "*()890"
cmd = "/usr/bin/kadmin -p account/admin -w ADminP@ssW0rd -q \"cpw -pw " + password + " " + username + "\""
try:
cmd_result = subprocess.Popen(cmd, shell=True, stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
message = cmd_result.stdout.read()
fd = open(logfile, 'a')
fd.write(str(datetime.now()) + " cmd : " + cmd + " result : " + message + " \n")
if message.find("already exists") != -1:
result_code = "failed"
result_message = username + " is already exists"
elif message.find("does not exist") != -1:
result_code = "failed"
result_message = username + " is not exist"
elif request.method == 'PUT':
if message.find("changed.") == -1:
result_code = "failed"
result_message = message
elif request.method == 'GET':
auth_time = "[never]"
message = re.sub("Last successful authentication: .*", "Last successful authentication: " + auth_time, message)
result_message = message
fd.close()
except subprocess.CalledProcessError as e:
result_code = "failed"
result_message = e.returncode
message = {'result': result_code, 'message': result_message}
fd.close()
return json.dumps(message)
@app.route('/krb/user', methods=['GET'])
def showAllUsers():
result_code = "success"
result_message = "ok"
if request.method == 'GET':
cmd = "/usr/bin/kadmin -p account/admin -w ADminP@ssW0rd -q \"getprincs\" | grep -v \"\/\""
try:
cmd_result = subprocess.Popen(cmd, shell=True, stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
result_message = cmd_result.stdout.read()
except subprocess.CalledProcessError as e:
result_code = "failed"
result_message = e.returncode
message = {'result': result_code, 'message': result_message}
return json.dumps(message)
'Setup' 카테고리의 다른 글
| Kerberos setup - 3 (MacOS User) (907) | 2019.12.09 |
|---|---|
| Kerberos setup - 2 (Kerberos Client) (928) | 2019.12.09 |
| Kerberos setup - 1 (Kerberos Server) (1901) | 2019.12.09 |
| OpenVPN setup - 3 (OpenVPN Client for VPC Tunnel) (1427) | 2019.12.09 |
| OpenVPN setup - 2 (OpenVPN Server) (1394) | 2019.12.09 |